The new IT Security Act 2.0
In a digitally connected world, a secure IT infrastructure is more important than ever. Companies classified as "critical infrastructures" (KRITIS) are considered particularly worthy of protection. If a KRITIS company experiences a failure, it can lead to significant supply shortages and potentially endanger public safety.
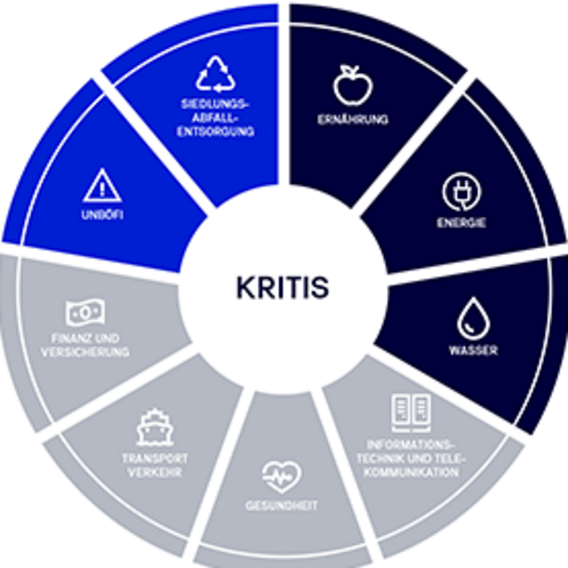
Until recently, seven different sectors were classified as KRITIS in Germany. These include industries such as energy, water, food, telecommunications, healthcare, and finance. With the introduction of the IT Security Act 2.0 (IT-SIG 2.0), the sectors of municipal waste disposal and companies of special public interest (UBI/UNBÖFI) have been added.
The IT-SiG 2.0, by lowering the thresholds in the KRITIS regulation, now requires significantly more organizations to implement effective measures to enhance their IT security. The fundamental aim is to encompass all companies that provide services and products to more than 500,000 people.
