Our services support you along the entire process - modular or holistic:
Workshops
- For targeted preparation for C-ITS certification.
Conception & preparation
- Conformity assessment of technical infrastructures when setting up a public key infrastructure (PKI).
- Evaluation of existing security procedures and categorisation of the current security level.
Testing & conformity assessment
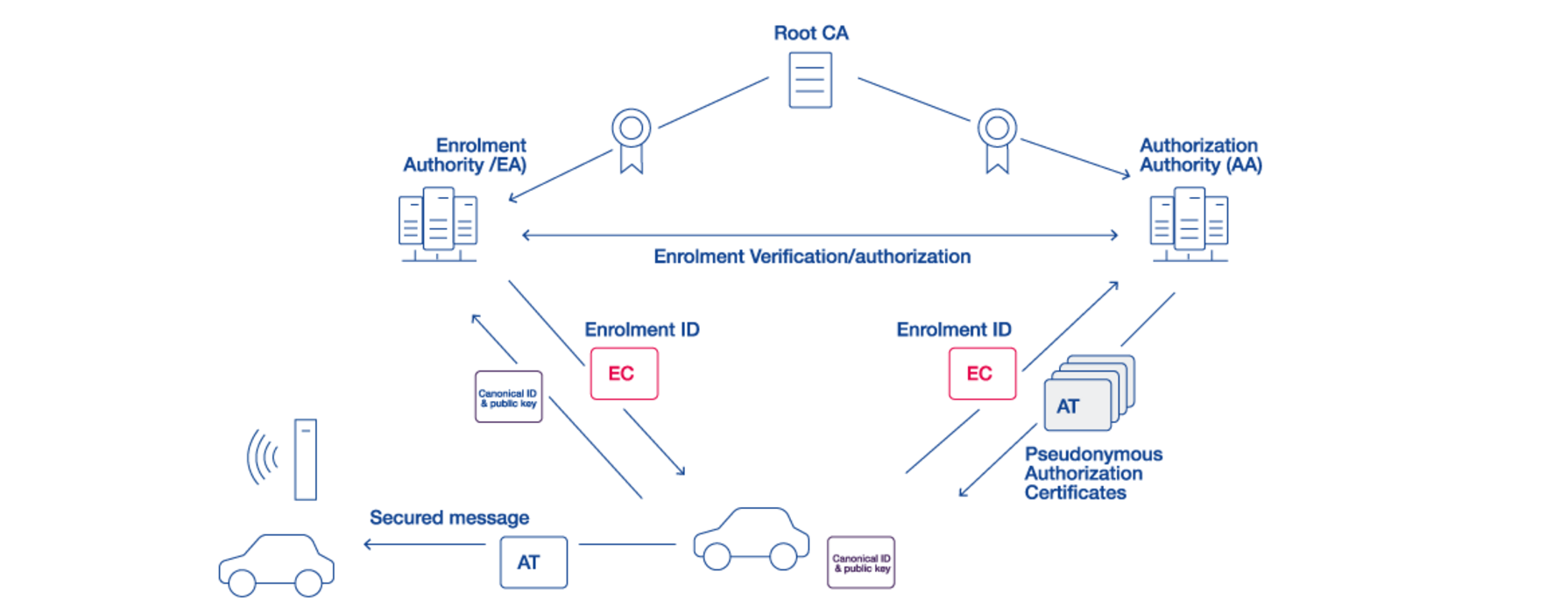
As an "Accredited PKI Auditor", we audit Root CAs, Enrolment Authorities (EA) and Authorisation Authorities (AA) in accordance with the Certificate Policy (CP) and thus Annex 3 of the Delegated Act (DA).
- Root CA: The Root CA is the root certification authority that forms the trust anchor for the EA and AA and authorises the EA or AA to issue certificates below the Root CA.
- Enrolment Authority (EA): The EA authenticates the C-ITS stations and enables them to access ITS communication (in the direction of the AA). For this purpose, the C-ITS station authorises the enrolment credential (EC), which the EA sends to the C-ITS station after successful authentication.
- Authorisation Authority (AA): The AA issues binding proof to the C-ITS Station that certain ITS services may be used. For this purpose, the C-ITS station authorises the Authorisation Ticket (AT), which the AA sends to the C-ITS station on the basis of the trust in the EA.
Classification in the C-ITS trust model:
Root CA, EA and AA are categorised in the "C-ITS trust model". This represents a system that is responsible for the trust between the C-ITS stations. It is a Public Key Infrastructure (PKI) consisting of Root CAs, the C-ITS Point Of Contact (CPOC), the Trust List Manager (TLM), Enrolment Authorities (EAs), Authorisation Authorities (AAs) and a secure network.
Certification & re-certification
Review of processes and documentation in accordance with the requirements of the EU Commission (Delegated Act).
Evaluation & certification of your C-ITS stations and crypto modules according to Common Criteria and relevant protection profiles.